QUESTION 127
You need to enable and configure Microsoft Defender ATP to meet the security requirements. What should you do?
Explanation/Reference:
Implement and manage threat protection
Testlet 3
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.
Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York.
The company has the offices shown in the following table.
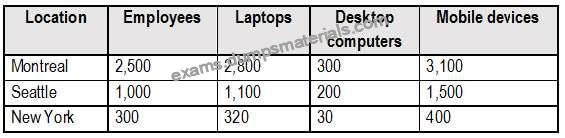
Contoso has IT, human resources (HR), legal, marketing, and finance departments. Contoso uses Microsoft
365.
Existing Environment
Infrastructure
The network contains an Active Directory domain named contoso.com that is synced to a Microsoft Azure Active Directory (Azure AD) tenant. Password writeback is enabled.
The domain contains servers that run Windows Server 2016. The domain contains laptops and desktop computers that run Windows 10 Enterprise.
Each client computer has a single volume.
Each office connects to the Internet by using a NAT device. The offices have the IP addresses shown in the following table.
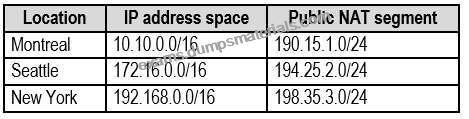
Named locations are defined in Azure AD as shown in the following table.
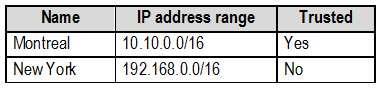
From the Multi-Factor Authentication page, an address space of 198.35.3.0/24 is defined in the trusted IPs list.
Azure Multi-Factor Authentication (MFA) is enabled for the users in the finance department.
The tenant contains the users shown in the following table.
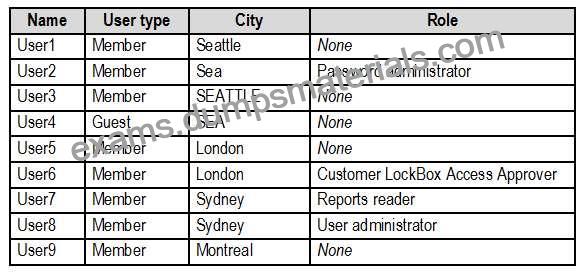
The tenant contains the groups shown in the following table.
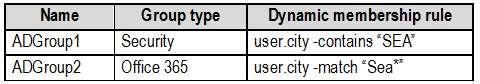
Customer Lockbox is enabled in Microsoft 365.
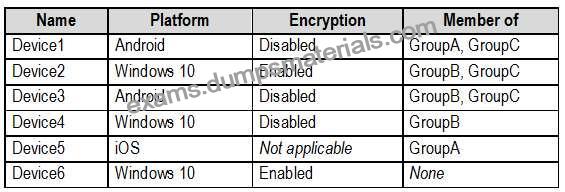
Microsoft Endpoint Manager Configuration
The devices enrolled in Microsoft Endpoint Manager are configured as shown in the following table.
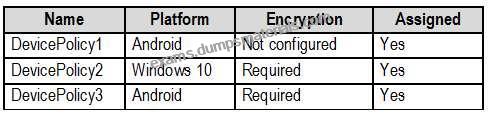
The device compliance policies in Microsoft Endpoint Manager are configured as shown in the following table.
The device compliance policies have the assignments shown in the following table.
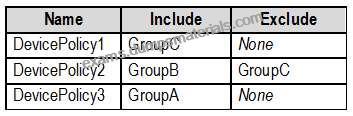
The Mark devices with no compliance policy assigned as setting is set to Compliant.
Requirements
Technical Requirements
Contoso identifies the following technical requirements:
* Use the principle of least privilege
* Enable User1 to assign the Reports reader role to users
* Ensure that User6 approves Customer Lockbox requests as quickly as possible
* Ensure that User9 can enable and configure Azure AD Privileged Identity Management Implement and manage threat protection Question Set 4








